Introduction:
Welcome to a world where technology meets luxury in the most extraordinary way. In this blog post, we will delve into neuromorphic computing, an emerging field that promises to revolutionize the way we interact with machines and experience luxury.
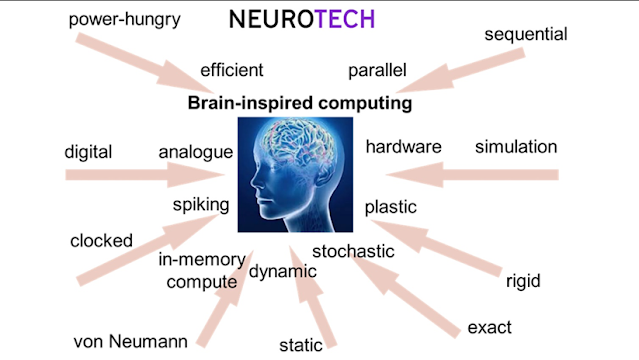
The fact that neuromorphic engineering draws inspiration from our understanding of the composition and functions of the brain sets it different. What is known about the functioning of the brain is translated into computer systems through neuromorphic engineering. The main areas of research have been the role of neurons in cognition and the analog nature of biological computation.
1. The Working Of Neuromorphic Computers, Hardware, Software
Neuromorphic computing works by simulating the behavior of biological neural networks using artificial neurons and synapses. These artificial neurons are organized into layers, similar to the structure of the brain's cortex. Information is processed in a massively parallel manner, with neurons communicating through spikes or pulses of activity.
1.1. Working of Neuromorphic computing
Neuromorphic technology seeks to mimic the structure and function of the human brain in computing systems. It typically uses analog circuits to simulate the behavior of neurons and synapses. Neuromorphic systems can perform certain tasks, such as sensor data processing, with significantly lower energy consumption compared to traditional computers.
1.1.1. Neurons
Artificial neurons receive input signals, perform computations, and produce output signals. They can be modeled to exhibit various characteristics, such as firing thresholds and activation functions.
1.1.2. Synapses
Connections between neurons, analogous to biological synapses, transmit signals and modulate the strength of connections. Synaptic weights determine the influence of one neuron on another.
1.1.3. Spiking Activity
Neurons communicate through spikes or action potentials, which are brief electrical impulses. Spike-based communication enables efficient event-driven processing and can mimic the asynchronous nature of biological neural networks.
1.2. Hardware Architecture
Neuromorphic hardware architectures are optimized for energy efficiency and parallel processing. They may consist of specialized chips designed to accelerate neural network simulations or implement neuromorphic algorithms directly in hardware.
Neuromorphic hardware represents a departure from traditional computing methods. It mimics the parallel and non-linear processing of the human brain, allowing for more efficient and intelligent systems. It's a paradigm shift that holds immense promise for a wide range of applications, from artificial intelligence to robotics.
1.2.1. Spiking Neural Network
SNN neurons receive inputs from other neurons or external sources. Instead of continuously updating their activation values, SNN neurons accumulate input signals over time until they reach a certain threshold, at which point they generate a spike or action potential.
1.2.2. Neuromorphic Chip
Neuromorphic chips are specialized hardware designed to implement neuromorphic computing principles efficiently. These chips are inspired by the structure and functioning of the human brain, aiming to emulate its neural networks and cognitive capabilities. Several companies are actively involved in developing neuromorphic chips and related technologies.
1.2.2.1. IBM TrueNorth
IBM has been a pioneer in neuromorphic computing with its TrueNorth chip, which features a massively parallel architecture inspired by the brain's structure. IBM Research continues to advance neuromorphic hardware and software, exploring applications in AI, robotics, and neuroscience.
1.2.2.2. Intel Loihi
Intel has invested in neuromorphic computing through its Loihi chip, which integrates thousands of artificial neurons and synapses. Intel Labs is actively researching neuromorphic architectures and algorithms for applications ranging from autonomous vehicles to cybersecurity.
1.2.2.3. SpiNNaker
SpiNNaker (Spiking Neural Network Architecture) is a project led by the University of Manchester, which has developed custom neuromorphic chips for large-scale simulations of spiking neural networks. The SpiNNaker platform is used for research in neuroscience, robotics, and machine learning.
1.3. Software Technology
Several software frameworks and tools are used in neuromorphic technology to design, simulate, and program neural networks on neuromorphic hardware. Some notable examples include
1.3.1. SpiNNaker Software
SpiNNaker provides a software infrastructure for programming and simulating large-scale spiking neural networks on the SpiNNaker neuromorphic hardware platform. It includes tools for network configuration, simulation management, and real-time visualization of neural activity.
1.3.2. NEST
One popular simulator for large-scale neural networks is the Neural Simulation Tool (NEST). NEST can be used to mimic spiking neural networks and investigate their behavior on a variety of computing systems, including neuromorphic devices, even though it was not created especially for neuromorphic hardware.
1.3.3. Brian
Brian is a Python-based simulator for spiking neural networks, offering a user-friendly interface for network construction, simulation, and analysis. While primarily used for research and education, Brian can be adapted to interface with neuromorphic hardware platforms for real-time experimentation.
1.3.4. Nengo
A Python package called Nengo is used to create and simulate large-scale brain models, such as spiking neural networks. It offers resources for designing brain circuits that make biological sense and transferring them to neuromorphic hardware architectures, including the Loihi processor from Intel.
2. Applications of Neuromorphic Technology
Neuromorphic technology has a wide range of applications across various fields.
2.1. Artificial Intelligence
Neuromorphic chips and algorithms are used to develop AI systems capable of performing tasks such as pattern recognition, object detection, and natural language processing. These systems leverage the brain-inspired architecture and efficient event-driven processing of neuromorphic hardware to achieve high performance with low power consumption.
2.2. Robotics
Neuromorphic computing enables the development of intelligent robots capable of autonomous decision-making, sensorimotor control, and adaptive learning. Neuromorphic hardware and algorithms are used to implement neural networks for perception, navigation, and manipulation tasks in robotic systems.
2.3. Brain-Computer Interfaces (BCIs)
Neuromorphic technology plays a key role in the development of BCIs that enable direct communication between the brain and external devices. These interfaces use neural signals recorded from the brain to control prosthetic limbs, assistive devices, and virtual reality applications, enhancing mobility and communication for individuals with disabilities.
Conclusion
Neuromorphic technology represents a groundbreaking approach to computing, drawing inspiration from the intricate workings of the human brain to create highly efficient and adaptive systems. Through the emulation of neural networks and the utilization of event-driven processing, neuromorphic chips and algorithms offer significant advantages in terms of energy and efficiency.
Author Bios:
- Dr. K. Amudha
- Dr. P. Elayaraja
- M. Mohankumar




Comments
Post a Comment